Docker is an open-source platform that lets you build, deploy and run portable container-based applications. The concept of containers was around for some time, but it was Docker that made this technology popular and widely accepted. Irrespective of the host operating system, container applications would run exactly the same everywhere. This helps make the process of software development, testing, and deployment simple and fast. Developers need not have to spend their time debugging and fixing dependency issues. Agility, scalability, cost-effectiveness are some of the other major benefits you get to enjoy by running applications in containers. All these factors have boosted the adoption rate of Docker over the past few years.
Why is Docker Container Security an Important Factor?
According to Gartner by 2022, around 75% of the organization worldwide will run containerized applications in production. Even though most of the container runtime engine such as Docker offers a more secure environment than the traditional model, the organizations running containerized applications need to make sure that their containers remain secure. A single compromised Docker container can open the doors to a cyber attack and can result in all the containers getting infected with some sort of malicious program. Attackers can even infect the host system, thus causing severe damage.
As a result, it is essential to make sure that all your docker containers remain secure from any breach by following some of the best Docker container security practices.
Docker Security Best Practices to Keep your Containers Secure
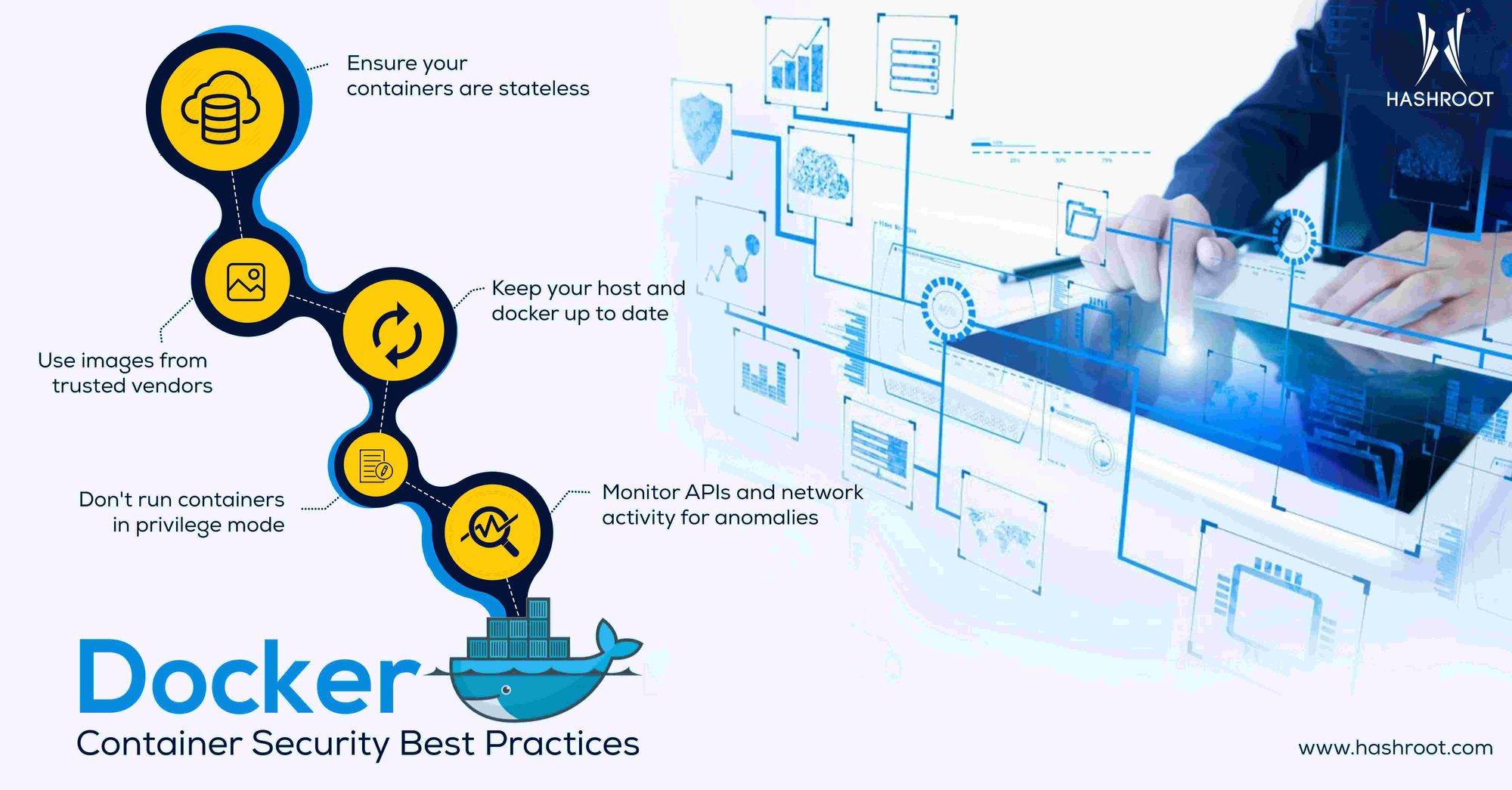
Docker is very complex and there are chances that organizations might make mistakes while configuring it. Even most of the companies that use Docker containers to develop applications don't have a well-defined Docker security strategy that helps mitigate docker container security vulnerabilities. Attackers will misuse such vulnerabilities to breach containers and even infect the host system.
Here are some of the Docker security best practices that you should follow in order to prevent Docker container security breaches.
Regular Update
Make sure to keep your Docker platform and containers up to date. Updating the underlying host operating system is equally important to prevent security vulnerabilities. Each update contains security patches and other enhancements that help protects your data and boost the system's performance. By carrying out regular updations and hardening the host will help secure all the containers in the environment.
Use Trusted Images Only
Docker lets you pull images from online registries without validating them. This can be hazardous and can leave your Docker containers vulnerable to attacks. Therefore, it is always recommended to validate the authenticity of container images before pulling them.
If your desired docker container image is available on the official Docker Hub, it would be better to go ahead with that instead of online third-party registries. All the container images in Docker Hub are trusted and you don't need to worry about its authenticity. As an additional security Docker allows users to add another layer of protection, by signing images. Docker Notary is a tool that lets users verify the origin of content by checking the digital signature of the image.
Monitor Network Activities for Anomalies
Docker containers use APIs to communicate with each other. Studies have revealed that network anomalies and poorly configured APIs can help attackers to gain access to containers and even the host system. By configuring APIs securely and regularly tracking the container activities and network connections that are being established, the probability of an attack can be reduced to a great extent.
Reduce container size
Minimizing container size helps to reduce the possibility of any attacks or security breaches. Using a smaller base image is one of the easiest and convenient ways to reduce the size of containers. This helps reduces the attack surface and decreases the probability of any vulnerabilities coming up. Smaller container size not only ensure better security but also ensures faster deployment and transfer as well.
Don't run containers in privilege mode
It is advised not to run Docker containers with root permissions. Running containers in privilege mode makes the application vulnerable to security attacks. By running containers with root permissions you are granting containers all the privileges a host has. Privilege mode containers can access the kernel and hardware resources inside the host, which normal containers don't have access to. Such privilege containers can be targeted by attackers to gain access to the host system.
Ensure your containers are stateless
Containers are designed to remain stateless and immutable. Stateless containers do not store any data inside them. All the data should be stored in a volume outside the container, so that you can shutdown or replace containers cleanly whenever required. This helps prevent data loss as well.
Conclusion
The docker adoption rate has increased significantly over the past years. Organizations all over the world have started adopting Docker container technology to simplify the process of application development and deployment. Even though Docker technology is much more secure, vulnerabilities can pop up anytime and organizations must be well prepared to identify them and fix them at the earliest. By following the Docker security best practices mentioned in this article, organizations can ensure their Docker containers security.
It is always better to make use of an active monitoring system to regularly scan for any sort of vulnerabilities. HashRoot has immense experience in providing Docker consulting services to customers all over the world. We can help keep your Docker containers protected against any form of cyberattacks.
Related Blogs
Migrating to the Cloud: Why Move from On-premise to Cloud?
Factors to Consider While Choosing A DevOps Service Provider
Why do Enterprises Need to Adopt Multi-Cloud Strategy?
Top 7 benefits your business could derive from a Cloud Managed Service Provider

